Exam Sections and Sub-task Objectives
1 Implement network infrastructure to support WLANs
1.01 Implement Catalyst configuration (VLANs, VTP, STP, Trunk, Portchannel,LB..)
1.02 Implement network connectivity in WLC
1.03 Implement network connectivity in LAP (local mode, hreap + local switching)
1.04 Implement network connectivity in AP (multiple vlans, vs single vlan)
1.05 Configure client to connect/authenticate to SSIDs
1.06 Implement DNS, DHCP, NTP
1.07 Implement QoS to support voice services over the switching infrastructure
1.08 Implement basic IP routing
1.09 Troubleshoot network infrastructure to support Wireless
2 Implement Autonomous Infrastructure
2.01
Configure WDS
2.02
Implement local radius
2.03 Implement SSID/MBSSID as needed: Security policies and Bridging groups
2.03 (a) Security policies
2.03 (b) Bridging groups
2.04 Implement radio roles
2.05 Implement antenna settings
2.06 Implement association filters
2.07 Implement and control management access
2.08 Implement MFP
2.09 Implement multicast settings
2.1 Implement QOS
2.11 Implement peer to peer blocking
2.12 Troubleshoot bridge connectivity problems
2.13 Convert Autonomous to LWAP
3 Implement Unified Infrastructure
3.01 Implement Interface settings
3.02 Implement mobility groups
3.03 Implement WLANs
3.04 Implement multicast settings
3.05 Implement and control management access
3.06 Implement controller redundancy/fallback
3.07 Implement discovery mechanisms
3.08 Implement AutoRF to adapt to site requirements
3.09 Check and validate current channel/power settings
3.1 Validate trap generation, notifications in WCS/WLC
4 Implement Unified Controllers and AP's
4.01 Implement peer to peer blocking
4.02 "Implement Security
4.02 (a) WPS settings
4.02 (b) MFP/AP authentication
4.02 (c) AP authorization"
4.03 Implement QOS
4.04 Implement local EAP authentication (against local user list, and external LDAP)
4.05 Implement L3 security policies (Webauth, pass-through)
4.06 Implement wired and wireless Guest
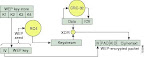
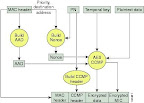
4.07 Implement L2 security policies (802.11i, static dynamic WEP, mac filtering, etc..)
4.08 Implement Local DHCP services for clients
4.09 Implement AAA (WLC to Radius/LDAP)
4.1 Troubleshoot client connectivity problems
5 Implement Unified WCS and Location
5.01 Implement controllers to WCS
5.02 Create and deploy template, template groups
5.03 Prepare building/floor map
5.04 Create floor coverage proposal
5.05 Implement location server
5.06 Tune location services given needs (tag tracking, notifications, timers)
5.07 Validate client connectivity/troubleshoot client via WCS/WLC
5.08 Validate location information in WCS/WLC
5.09 Validate security events with WCS/WLC
5.1 Validate location information in WCS/WLC
5.11 Validate trap generation, notifications in WCS/WLC
5.12 Validate client connectivity/troubleshoot client via WCS/WLC
6 Implement Voice over Wireless
6.01 Implement support for 7920/7921 deployments, for both Unified and Autonomous
6.02 Implement QoS settings:
6.02 (a) Voice/Video
6.02 (b) EDCA
6.03 Audit voice deployment